In yesterday`s discussion we took a look at three ways in which cyber criminals will attack your computer, today we continue with the discussion.
4. Phishing:
The attacker sends bait, often in the form of an email. It encourages people to share their details. For example, you get an email like this:
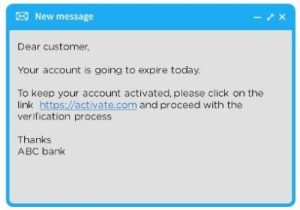
If someone is a customer of ABC bank, he would probably open the link and enter the details. But these kinds of emails are always phishing. Banks do not send emails like this.
5. Eavesdropping:
Attacker observes traffic on your system and the work you are doing. The attacker can monitor you in three ways:
1. Email monitoring
2. Which websites you visit
3. What items you download
6. SQL injection:
As the name suggests, an SQL injection vulnerability allows an attacker to inject malicious input into a SQL statement. This type of attack happens only on websites. The best example would be www.facebook.com. There is a database stored on the Facebook website. The hackers get into that database and sign in using someone else’s username and password.
7. Password attack:
To crack a password or find a password, hackers employ the following techniques:
Dictionary attack: In this method, they handle every password that is possible through the dictionary
Brute force: It is a trial and error method used to decode the password or data. This attack takes the most amount of time.
Keylogger: As the name suggests, keylogger records all the hits on the keyboard. Most people use it to get passwords and account details
Shoulder surfing: The attackers observe the user’s keyboard by looking over the user’s shoulder.
Rainbow table: There are rainbow tables that contain precomputed hash values. Attackers use this table to find the user’s password.
8. Social engineering:
Attackers create social situations that encourage you to share your password. For example, let’s say that you are out of your office, and you get a call. The person says that he is from the IT department and they have found out that your system has been compromised. He asks you to share your password. You might believe him and share your password. However, the caller was, in fact, a hacker, and now he has your password. Now that he has access, he can compromise your organization’s data. The best way to avoid the effects of social engineering is to learn your organization’s protocol regarding password sharing.



0 Comments